
The General Data Protection Regulation (GDPR) is one of the world’s strictest data privacy laws and requires privacy professionals around the globe to design and implement comprehensive compliance programs. In the past year, I developed a series of resources and training courses to assist privacy professionals with this complex task.

200+ pages of the GDPR summarized into 1 page! Download it for free here. This one page visual summary of GDPR will help you and your workforce understand many of the key elements associated with this law including Territorial Scope, Lawful Processing, Rights of Data Subjects, Enforcement and more.
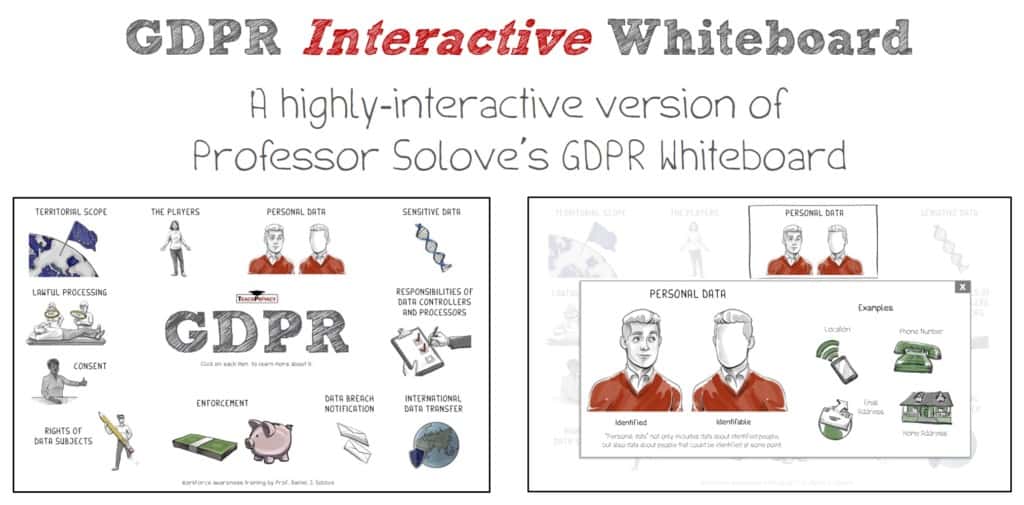
I created a new highly-interactive version of the GDPR Whiteboard (~5 mins) — a computer-based module that can readily be used on internal websites to raise awareness and teach basic information about GDPR. It can also be used in a learning management system (LMS)
The GDPR Interactive Whiteboard adds a new level of engagement to the analog GDPR Whiteboard. and can be used in tandem with the analog version or in lieu of it.

A Guide to GDPR Training will answer many of your questions about implementing workforce privacy awareness training.
The GDPR mandates that all staff “involved in the processing operations” receive privacy awareness training. In general, the Data Protection Officer (DPO) is tasked with ensuring that all training requirements have been fulfilled. A comprehensive GDPR training program should include:
- basic privacy awareness training for your general workforce
- advanced training for personnel who need more detailed knowledge of GDPR
- role-based training specific to an individual’s job function.
I have several training courses to help organizations meet the GDPR requirements, such as the ones below plus courses on Privacy by Design, vendor management, risk and trust, and other important privacy topics.

This course provides an overview of the GDPR. It also explains the importance of GDPR compliance and the severe penalties that may be imposed for non-compliance. It is suitable for both lawyers and non-lawyers . This course can also be offered in conjunction with other courses in our series – Privacy Shield and European Union Privacy Law.
COURSE OUTLINE:
- Structure
Scope
Personal Data
Sensitive Data
Data Controllers and Data Processors
Supervisory Authority
Enforcement
Rights and Responsibilities
International Data Transfer
- Rights and Responsibilities
Transparency
Purpose Specification and Minimization
Consent
Right to Erasure
Right to Data Portability
Data Protection by Design
Data Protection Impact Assessments
Record of Data Processing Activities
Data Breach Notification
- International Data Transfer

This course (~20 minutes or 30 minutes) is designed to provide basic privacy awareness to the workforce of global organizations. I updated this program for GDPR. The course focuses on three main issues:
- Why is privacy important?
- What is personal data?
- How do we protect privacy?
COURSE OUTLINE:
- The Purpose of this Training
Personal Data
People Care About Privacy
Your Role
- Why We Protect Personal Data
Respect
Preventing Harm
Trust
Reputation
Legal Compliance
Contractual Compliance
- What is Personal Data?
Identifying Personal Data or PII
Sensitive Data
- Data Collection
Lawful Basis
Data Collection Limitation
- Data Handling and Processing
Limited Access
Confidentiality
Security Safeguards
- Use of Personal Data
Purpose Specification
- Individual Knowledge and Participation
Notice
Access and Correction
Consent
Right to Erasure
Right to Data Portability
- Transfer and Sharing of Data
International Transfers of Data
Sharing Data with Third Parties
- Accountability
Privacy by Design
Ask the Privacy Office

Please check out our humorous 1-minute video vignette about the GDPR.
CARTOONS























